
DevOps practices have brought remarkable improvements in efficiency and velocity across the Software Development Life Cycle (SDLC), from artifact creation to deployment. However, a critical frontier remains: the automation of Governance, Risk, and Compliance (GRC).
To facilitate continuous GRC through automation, this blog post introduces the concept of a Strongly Identifiable Binary (SIB). This Binary Identity is formed by coupling immutable provenance metadata with immutable binary cryptographic hashes and the immutable original binary storage location within the artifact repository. An SIB sets the foundation for a Zero Trust Architecture in the development phase of the SDLC.
The need for automated GRC
The past decade has witnessed the profound impact of DevOps on software development and delivery. Organizations have embraced practices like Continuous Integration (CI), Continuous Delivery (CD), and DORA metrics to accelerate their release cycles, improve collaboration, and enhance the overall quality of their software products.
This journey has focused on automating various stages of the SDLC, leading to significant gains in efficiency and speed. While DevOps has revolutionized how software is built and deployed, one critical aspect has remained too often manual and reactive—namely, that the software build and deploy process adheres to governance, risk, and compliance requirements.
As GenAI accelerates the pace of software development, the traditional, periodic approach to GRC is increasingly inadequate, creating bottlenecks and potential risks, especially in large enterprises with complex regulatory landscapes.
The next logical evolution in this journey is the comprehensive automation of GRC processes, integrating them seamlessly into the DevOps and IT Service Management pipeline to achieve what is termed “continuous GRC”. This shift promises to address the inherent challenges of maintaining security and compliance in a fast-paced development environment, ultimately leading to more secure, reliable, and compliant software releases.
Expected business outcomes
The automation of GRC processes throughout the SDLC offers a multitude of positive business outcomes, particularly for large enterprises. One of the most significant advantages lies in the reduction of costly, late-stage GRC violations.
The discovery of a GRC violation—such as detecting that a dependency’s origin is from a non-approved repository—right before a production deployment in a monthly or quarterly release cycle can be exceptionally expensive, often outweighing all the efficiency gains achieved earlier in the SDLC.
By implementing continuous GRC automation, organizations can identify and remediate potential violations much earlier in the development process, preventing these costly last-minute surprises and ensuring smoother, more predictable releases. This “shift-left” approach aligns with DORA metrics and continuous delivery best practices by ensuring that security and compliance are considered from the outset, rather than being bolted on as an afterthought. In fact, it’s one of the DORA capabilities: Pervasive Security. This leads to more secure and resilient software products, which is particularly critical in today’s threat landscape, where software supply chain attacks (e.g., the 2025 SpotBugs key leak) and vulnerabilities are increasingly prevalent and can have severe financial and reputational consequences.
As such, continuous GRC automation fosters a stronger security posture by embedding security checks and compliance requirements directly into the development pipeline.
By automating GRC, organizations can also achieve improved operational efficiency by eliminating manual, time-consuming compliance tasks. This frees up valuable resources, allowing development, security, and compliance teams to focus more on strategic initiatives and innovation.
Moreover, continuous GRC automation provides enhanced visibility and reporting into an organization’s risk and compliance posture. Real-time dashboards and automated reports offer stakeholders a clear, up-to-date view of key GRC metrics, enabling informed decision-making and facilitating communication with auditors and regulatory bodies.
How a Strongly Identifiable Binary (SIB) supercharges continuous GRC
At the heart of continuous GRC through automation lies the concept of a Strongly Identifiable Binary (SIB).
An SIB represents a paradigm shift in how software artifacts are managed and secured throughout their lifecycle. An SIB is fundamentally a software binary, artifact, or application that contains comprehensive provenance information gathered precisely at the demarcation plane—where human-readable source code is transformed into machine-executable binary instructions— between the source code and the resulting binary.
This critical juncture in the SDLC is where the transformation from human-readable code to machine-executable instructions occurs, making the information captured here uniquely valuable for establishing trust and ensuring integrity.
The Binary Identity of an SIB is composed of three immutable elements:
- Immutable provenance metadata
- Immutable binary cryptographic hashes
- Immutable original binary storage location within the artifact repository
Immutable provenance metadata
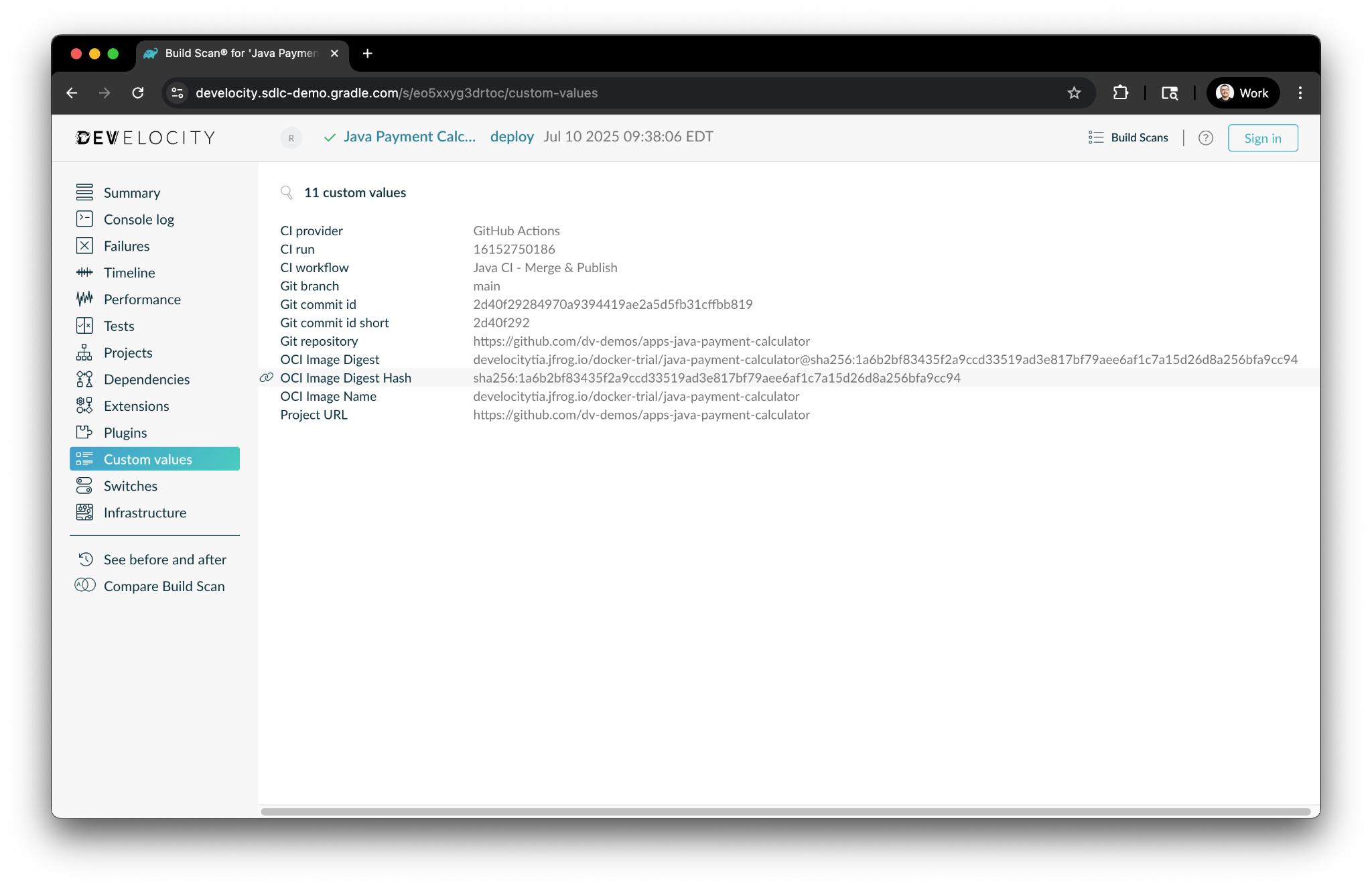
Immutable provenance metadata can include elements like the artifact digest, artifact location, source control information, and more
Immutable provenance metadata encompasses a detailed record of the entire artifact creation process. This includes not only the source code repository details (such as commit IDs and branches) but also a complete inventory of all the toolchains involved in the build process. This extends to the specific versions of compilers, linkers, build tools, different types of tests and the entire CI environment used to produce the binary.
It captures information about all first-party code and dependencies, as well as all third-party dependencies, ensuring a comprehensive understanding of the software’s composition not only at runtime but also at compile time.
Immutable binary cryptographic hashes
Immutable binary cryptographic hashes, such as SHA-256 hashes, provide a unique and tamper-proof digital fingerprint of the binary itself. Any alteration to the binary, no matter how small, will result in a completely different hash value, allowing for definitive verification of the binary’s integrity.
Immutable original binary storage location within the artifact repository
Finally, the immutable original binary storage location within the artifact repository provides an auditable and the starting lineage point for an SIB throughout its lifecycle. This combination of immutable provenance, cryptographic hashes, and storage location enables the establishment of a robust Binary Identity and Binary Lineage, which is essential for building a Zero Trust architecture across the entire SDLC.
Artifact provenance: The unseen hero of GRC automation
While the Software Bill of Materials (SBOM) has become a common means of understanding the components within a software artifact, it represents only a subset of the comprehensive provenance information required for effective continuous GRC automation.
Artifact provenance, in its fullest form, goes far beyond simply listing the ingredients; it provides a detailed narrative of the artifact’s entire journey from source code to binary.
Unique and critical provenance information is gathered from both the source code and the machine-readable binary artifacts on the demarcation plane, and includes a complete record of all the toolchains involved in the artifact creation process.
Knowing the specific versions of compilers, linkers, and build tools used is essential for reproducing the binary and for understanding potential vulnerabilities that might be specific to those tools. Provenance tracking captures all first-party code contributions and first-party dependencies, providing accountability and traceability back to the developers across organizations.
Critically, it also includes a detailed inventory of all third-party dependencies, along with their specific versions and sources, origin, and licensing, enabling organizations to proactively identify and manage potential security and licensing risks associated with these external components.
The CI environment itself, including build agents, configurations, and environment variables, plays a significant role in the final artifact. Provenance information captures these details, ensuring that the build process is transparent and reproducible.
Finally, artifact promotion enrichments, which might include additional metadata or signatures added as the artifact moves through different stages of the SDLC, are also part of the comprehensive provenance record. This rich and detailed provenance information reaches outside the scope of a basic SBOM, and is the key to enabling sophisticated GRC policies and automated enforcement throughout the software lifecycle.
Extending Zero Trust architecture to software development
SIB is fundamental to enabling a Zero Trust Architecture (ZTA) within the entire application lifecycle. ZTA operates on the principle of “never trust, always verify,” assuming that threats can exist both inside and outside the traditional network perimeter.
While this practice is becoming the de facto standard for application production runtime, it is yet to be adopted widely for the application build process and toolchain environment.
In the context of software development and CI/CD/IT Service Management pipelines, this means that no software artifact should be implicitly trusted, regardless of its origin or stage in the lifecycle.
The immutable Binary Identity, composed of the immutable provenance metadata, the immutable binary cryptographic hashes, and the immutable original binary storage location, provides artifact lineage and allows for continuous verification of every software artifact throughout its journey. At each stage of the SDLC, from development to deployment, the SIB’s identity can be verified against established policies and trusted sources.
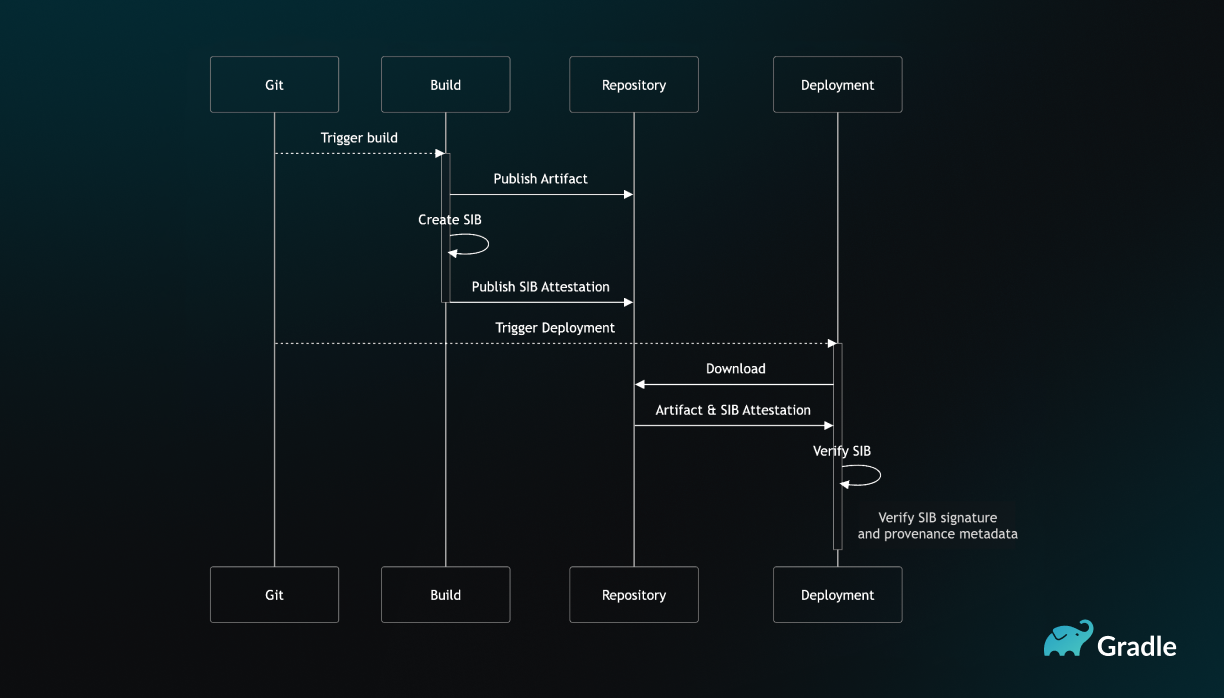
An SIB is created when the artifact is produced and can be verified at each step in your SDLC.
For example, before deploying an application to production, the platform can automatically verify the SIB’s cryptographic hash against the SIB attestation within a trusted registry to ensure its integrity. It can also verify the provenance metadata with the SIB attestation to confirm that the binary was built from authorized source code using approved toolchains, processes, and CI infrastructure, which conforms to the organization’s GRC requirements.
This continuous verification, enabled by the unique and immutable identity of SIBs, ensures that only trusted and compliant software artifacts are allowed to progress through every stage of the SDLC process, significantly reducing the risk of deploying vulnerable or malicious code. By eliminating implicit trust and enforcing explicit verification at every step, SIB technology provides a robust foundation for building a Zero Trust architecture in the modern software development environment.
Shifting-left GRC: Proactive awareness and troubleshooting
One of the key advantages of continuous GRC through automation, enabled by SIB technology, is the ability to shift-left the awareness and troubleshooting of GRC violations.
In traditional software development, security and compliance checks are often performed late in the SDLC, typically just before deployment. If violations are discovered at this stage, this can lead to costly delays and rework.
By integrating GRC automation into the CI/CD pipeline and leveraging the detailed provenance information embedded in SIBs, organizations can identify potential GRC violations much earlier in the development process.
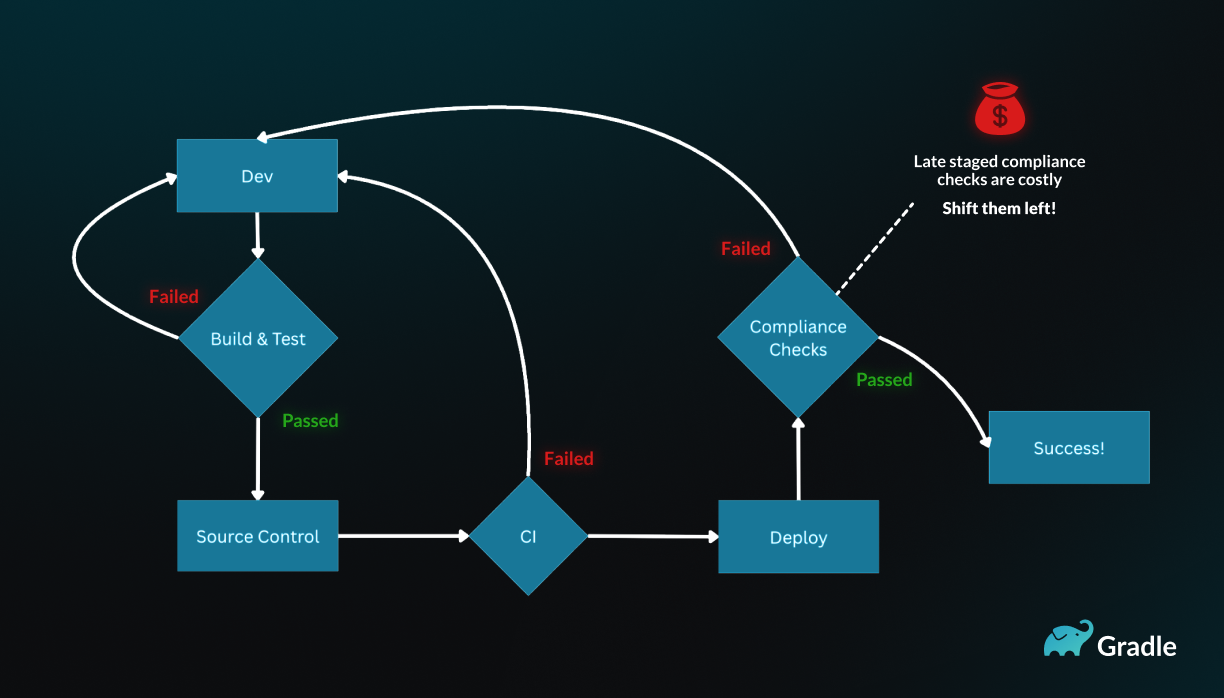
Unexpected late stage GRC violations delay deployments and cause expensive re-work.
For example, policies can be implemented to automatically check the provenance of third-party dependencies as soon as they are introduced into the codebase, flagging any known vulnerabilities or licensing issues. Similarly, security scans can be triggered automatically during the build process, and the results can be linked to or confirmed by the SIB’s provenance.
If a violation is detected, developers receive immediate feedback, allowing them to address the issue early on, when it is typically less costly and time-consuming to fix. This proactive approach not only improves the security and compliance of the software but also enhances developer productivity by preventing rework and ensuring that GRC considerations are integrated into the development process from the beginning.
The shift-left paradigm fosters a culture of security and compliance ownership among developers, leading to the development of more secure and compliant software by design at a lower cost.
Curated GRC policies with AI
Maintaining the velocity of software development while adhering to an ever-evolving landscape of GRC challenges and geopolitical complexities requires a dynamic and intelligent approach to policy management. Continuous GRC through automation can leverage AI assistance to curate GRC policies.
AI can play a crucial role in analyzing vast amounts of regulatory data, identifying relevant changes, and—with proper oversight—automatically updating GRC policies to reflect these new requirements. This ensures that organizations remain compliant with the latest regulations without the need for extensive manual effort.
Organizations can use AI to analyze historical data and identify patterns of GRC violations, providing valuable insights for proactively strengthening policies and controls. AI-powered tools can also assist in risk assessment by analyzing various data sources to identify emerging threats and predict potential compliance issues. This allows organizations to take proactive measures to mitigate these risks before they materialize.
Moreover, AI can personalize and contextualize GRC policies based on specific projects, teams, or applications, ensuring that the policies are relevant and effectively enforced. By leveraging AI to curate and maintain GRC policies, organizations can achieve a more agile and adaptive approach to governance, risk, and compliance, enabling them to maintain velocity while staying ahead of evolving challenges.
Automated GRC enforcement throughout the SDLC
The true power of continuous GRC through automation lies in its ability to provide automated GRC enforcement throughout the SDLC, encompassing every stage from the developer’s local environment to CI, CD, ITSM pipelines, and workflows.
- In the developer’s local environment, pre-commit hooks can be configured to verify code against security and compliance standards before it is even committed to the repository.
- During the CI process, automated builds can trigger static code analysis, vulnerability scanning, and license compliance checks, with failures preventing the artifact from progressing further.
- The CD pipeline can be configured to enforce deployment policies based on the SIB’s provenance and the results of previous GRC checks, ensuring that only authorized and compliant artifacts are deployed to production.
- GRC automation can extend into ITSM workflows, for example, by automatically creating tickets for any detected non-compliance issues or security vulnerabilities, such as Log4Shell, ensuring timely remediation.
This comprehensive and automated enforcement across the entire SDLC minimizes the risk of GRC violations slipping through the cracks and ensures that security and compliance are integral parts of the software development process, rather than isolated activities.
The impact of GRC automation on enterprise auditing
The introduction of SIBs has a profound and positive impact on auditing processes within large enterprises. Traditional auditing often involves manual and time-consuming efforts to verify the integrity and compliance of software systems.
Auditors need to gather evidence (which is often non-authenticated and non-verifiable) from disparate systems, review logs, and conduct interviews to gain assurance that the software deployed in production adheres to security policies and regulatory requirements. SIB technology streamlines and enhances this process significantly.
By providing an immutable and verifiable Binary Identity, SIBs offer auditors a single source of truth for understanding the complete lifecycle of a software artifact. The embedded provenance metadata provides a detailed and auditable trail of the artifact’s creation, including all the toolchains, dependencies, and processes involved.
Auditors can easily verify that the binary deployed in production is the same one that was built from the authorized source code and has passed all required security checks. The immutable cryptographic hashes ensure the integrity of the binary, confirming that it has not been tampered with since its creation. The immutable storage location provides a reliable lineage reference, allowing auditors to trace the artifact throughout its journey in the SDLC.
This level of transparency and verifiability significantly reduces the manual effort required for auditing, allowing auditors to focus on higher-level risk analysis and strategic recommendations. SIBs facilitate continuous auditing by providing readily available and trustworthy data about the software artifacts in use.
This enables organizations to move away from periodic audits to a more proactive and continuous monitoring approach, improving their overall GRC posture and reducing the risk of non-compliance.
GRC automation and Developer Productivity Engineering (DPE)
The relationship between GRC automation and Developer Productivity Engineering (DPE) is deeply intertwined and mutually beneficial. While seemingly distinct, both disciplines share the common goal of optimizing the software development lifecycle, albeit with different primary focuses.
GRC automation aims to ensure security, compliance, and risk management are seamlessly integrated into the SDLC, while DPE focuses on enhancing the efficiency, effectiveness, and satisfaction of software developers. When implemented effectively, GRC automation can actually boost developer productivity by reducing the burden of manual and often tedious compliance tasks. By automating security checks, policy enforcement, and evidence collection, GRC automation frees up developers to concentrate on writing code and delivering features, rather than spending time on compliance-related activities.
Furthermore, by shifting left security and compliance awareness, GRC automation helps developers identify and address potential issues early in the development process, preventing costly rework and delays later on. This proactive approach not only improves the quality and security of the code but also contributes to a smoother and more efficient development workflow.
Additionally, DPE practices can facilitate the adoption and effectiveness of GRC automation. By providing developers with the right tools, processes, and feedback mechanisms, DPE can make it easier for them to understand and adhere to security and compliance requirements. For example, integrating GRC scanning tools directly into the developer’s IDE or providing clear and actionable feedback on compliance violations can help developers write more secure and compliant code from the outset.
DPE’s focus on automation and streamlining workflows can create a more receptive environment for adopting GRC automation tools and processes. Ultimately, the relationship between GRC automation and DPE leads to a more secure, compliant, and efficient software development lifecycle, where developers are empowered to deliver high-quality software with confidence, knowing that security and compliance are seamlessly integrated into their workflow.
Conclusion
Continuous GRC through automation, with the introduction of Strongly Identifiable Binaries (SIBs), represents a critical evolution in modern software development. By leveraging the power of artifact provenance, immutable binary identities, and intelligent automation, enterprises can overcome the challenges of maintaining security and compliance in today’s fast-paced and complex environment.
The benefits are many, ranging from significant cost savings and improved operational efficiency to enhanced security posture, streamlined auditing, and increased developer productivity. As organizations continue to embrace DevOps, continuous delivery, and DORA to strive for greater agility, the adoption of continuous GRC through automation, built upon the foundation of SIB technology, will be paramount for achieving sustained success and building trust in their software products.
Learn how Develocity can help secure your pipelines and enable continuous GRC.

